Permissions and privileges can be
assigned to users directly or through membership in application roles or
Catalog groups. From another perspective, permissions and privileges can be
assigned explicitly or effectively. Effective permissions and privileges are
assigned indirectly through inheritance from application roles or Catalog
groups, which is the recommended approach for assignments.
Rules
for Inheritance for Permissions and Privileges
- Any permissions or privileges granted explicitly to a user override any permissions or privileges inherited from the application roles or Catalog groups to which the user belongs.
- If a user belongs to two application roles or Catalog groups and both are granted permissions, then the least restrictive permissions are given to the user.
For
example, if one application role allows Open access and another allows Modify
access, then the least restrictive access would be granted; in this example,
Open access.
- If a user belongs to Application Role X, and Application Role X is a member of Application Role Y, then any permissions assigned to Application Role X override any permissions assigned to Application Role Y. The same holds true if X and Y are Catalog groups.
- For example, if Marketing has Open permissions, Marketing Administrators, which is a member of Marketing, can have Full Control permission.
- If a Catalog group is specified along with an application role in the Permissions dialog in Presentation Services, then the Catalog group takes precedence.
For
example, suppose that for a certain object, the BIAdministrator role has
Read-Only permission and the Admin Catalog Group has Full Control permission.
If a user signs in who is a member of both the BIAdministrator role and the
Admin Catalog Group, then he is granted full access to the object.
- Explicitly denying access takes precedence over any other permissions or privileges.
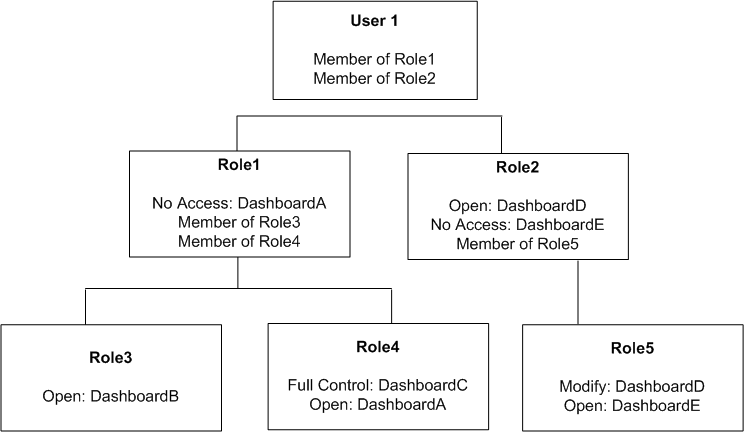
From the above fig effective permissions granted to user 1 are
- No access to DashboardA and DashboardE, because access is specifically denied.
-
Open access to DashboardB.
-
Full Control for DashboardC.
-
Modify access to DashboardD.
ReplyDeleteGreat Article. As I read the blog I felt a tug on the heartstrings. it exhibits how much effort has been put into this.
IEEE Projects for CSE in Big Data
Spring Framework Corporate TRaining
Final Year Project Centers in Chennai
JavaScript Training in Chennai